The research, recently shown at the BlackHat Asia conference in Singapore, describes how these devices were infected, what malicious plug-ins were used, and how the groups work together. Take a look at it.
Guerrilla malware-affected countries
The top 10 countries that are affected due to the Guerrilla malware are India, Argentina, Angola, Indonesia, Mexico, Philippines, Russia, South Africa, Thailand, and the US.
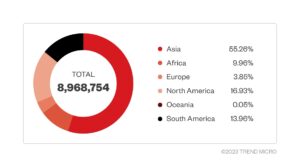
Guerrilla malware on 8.9 million Android devices
Analysts found the huge criminal operation, and some of the infrastructure of the attackers matches with that of the 2016 Triada trojan operation. Triada was a banking trojan that was found on 42 Android phone models from cheap Chinese brands that sell their goods all over the world.
The report said they found out about the Lemon Group for the first time in February 2022. Shortly after, the group is said to have changed its name to “Durian Cloud SMS.” But the architecture and methods of the attackers stayed the same.
Trend Micro hasn’t said more about how Lemon Group infects devices with malicious firmware that includes Guerilla, but it did say that the devices its experts looked at had new ROMs that had been re-flashed. The experts found more than 50 different ROMs that were infected with initial malware loaders and were aimed at different Android device manufacturers.
The primary plugin of the Guerrilla malware is in charge of loading additional plugins that have been created to carry out particular tasks, including:
- SMS plugin: The SMS Plugin is designed to intercept one-time passwords for WhatsApp, JingDong, and Facebook that are received via SMS.
- Proxy plugin and proxy seller: The Proxy Plugin enables attackers to use the victim’s network resources by establishing a reverse proxy from the infected phone.
- Cookie plugin/WhatsApp plugin/Send plugin and promotion platform: The Cookie Plugin is designed to extract Facebook cookies from the application data directory and send them to the C2 server. The compromised device is capable of hijacking WhatsApp sessions and sending out unwanted messages.
- Splash plugin: It is a type of malware that displays intrusive ads to users while they are using legitimate applications.
- Silent Plugin: The Silent Plugin is a tool that can install extra APKs that are sent from the C2 server or remove existing applications based on the given instructions. The installation and launch of the app occur in the background without any noticeable indication.
With these features, the Lemon Group can come up with different ways to make money. For example, they could sell compromised accounts, take over network resources, offer app-installation services, make fake ad impressions, offer proxy services, and provide SMS Phone Verified Accounts (PVA) services.














![[Exclusive] iQOO Z9, iQOO Z9x iQOO Z9 Turbo full specifications leaked ahead of China launch Thumbnail](https://www.91-cdn.com/hub/wp-content/uploads/2024/04/iQOO-Z9-series-leak-100x70.png)
